Microsoft Exchange 2010 Shadow Redundancy
FlexPod Datacenter with Microsoft Exchange 2013, F5 BIG-IP and Cisco Application Centric Infrastructure Design Guide. Active Directory (AD) is a directory service that Microsoft developed for Windows domain networks. It is included in most Windows Server operating systems as a set of.
Advanced Configuration - Exchange Database Agent. Table of Contents The Exchange Database Agent uses one main component to perform backup and restore operations from the Comm. Cell Console. From the Comm. Cell Browser, right- click Exchange Database, and then click Properties. Click Incremental or Differential and click OK. Transaction logs are not purged. Incremental - Specifies that each non- full Exchange database backup secures only that data that has changed since the last backup of any type.
Committed transaction logs are purged. Right- click Exchange Database and click All Tasks . Click Pre- Selected Backup Type and click OK. The next backup that is run must be a Full backup.
You’ve done your homework on moving from Exchange 2003 to Exchange 2010. Now it’s time to get to work. Here are the 12 main steps you need to take to get the job. Exchange 2010 Client Access Server (CAS) and Hub Transport Server (HT) Redundancy Providing High Availability and Failover in a Server or Site Failure. I can also track.
Symantec helps consumers and organizations secure and manage their information-driven world. Our software and services protect against more risks at more points, more.
VMware BEST PRACTICES Introduction Microsoft Exchange Server is the most widely used messaging platform in the world. It is used for approximately 1 percent of. Port Transport Protocol; 5300 : HA cluster heartbeat. 5301 : HA cluster general services. 5302 : HA cluster configuration. 5303 : HA cluster probing.
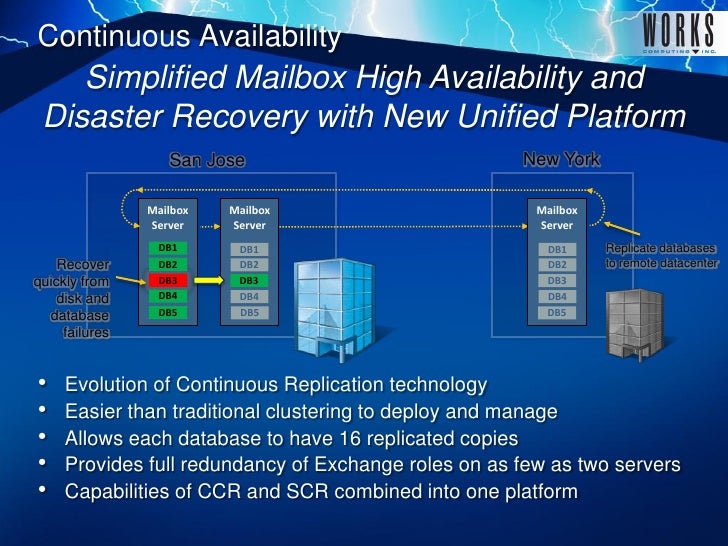
Applies to: Exchange 2. By default, all databases are automatically assigned to the default subclient. However, you can divide databases across one or more user- defined subclients to leverage your backups efficiently. From the Comm. Cell Browser, right- click the Exchange Database Agent on the source client, and click All Tasks > New Subclient. Click the Contents tab and then click Configure. Click Discover to display all databases.

Any of these errors occurring in the Exchange application event log before the specified date and time will be ignored, and any found after the specified date and time will be logged. This option can scan for the following file- level damage errors prior to continuing with the backup: -1.
JET. Follow the steps below to enable the event check option: From the Comm. Cell Browser, right- click the subclient you want to configure for Event Check, then click Properties. Click Use Event Check. Specify the date and time in the Last Event Check Time field. This will serve as the starting point to begin checking the Exchange application event log. Click OK. Applies to: Exchange 2. In some cases, it may be desirable to allow write operations on data being backed up to continue while the backup runs.
Enabling VSS for backups provides this capability. During a VSS backup, the free space needed on a volume for the shadow copy is related to the duration of the backup and the amount of changes being made to the data objects (files, databases) that are being backed up.
VSS snapshots capture and copy disk blocks that are being changed by other processes while the backup for a particular object is running. If the backup runs longer, or there is a lot of disk activity (files or databases being changed). This causes VSS to copy more data blocks and therefore, use more disk space.
VSS can be enabled for backups of local volumes in both clustered and non- clustered environments. If the operating system fails to create a shadow copy of the data a traditional backup of the data will be performed, and a corresponding message will appear in the Event Viewer. A consistency check of the database integrity will be performed by the system prior to backing up the data, and if the integrity check fails then the backup will fail. Ensure the Exchange database is mounted. From the Comm. Cell Browser, right- click the Exchange Database Agent on the source client and select Properties.
Select Use VSS. Click OK. Applies to: Exchange 2. By default, log files are truncated during backups. However, it may be desirable to keep log files from being truncated to preserve their original state if needed during a restore. This can be accomplished using the Copy Backup feature. From the Comm. Cell Browser, right- click the Exchange Database Agent , and then click Properties. Click Copy Backup.
Click OK. Applies to: Exchange 2. CCR backups continuously replicate the Exchange Database transaction logs residing on the active node of a CCR cluster to the passive node.
In the event of failover, the replicated database will be available to users, which reduces the frequency at which full backups must be taken and the volume of backup data and media usage, as well as shortening the time it takes to recover from failure. Starcraft 2 All In One Loader Operator here. No resources are shared and only one virtual server is used. Follow the steps below to enable cluster continuous replication backups: From the Comm. Cell Browser, right- click the Agent for the Exchange 2. Database that you want to configure for CCR backups, and then click Properties. Select the Use VSS and Backup from replica check boxes.
Select Backup on active node if passive node is unavailable if appropriate for your environment and if you intend to use backups from the active node to perform a CCR seeding operation of data to the passive node. Click OK. CCR options are configured. Subsequent backups for the agent will use VSS to perform a Shadow Copy backup of the replica database on the passive node of a CCR cluster. Applies to: Exchange 2. You can configure to restore the data to a Recovery Storage Group when you meet the following two conditions: The logical information in Active Directory about the storage group and the associated mailboxes is intact. You want to recover data from a single mailbox, a single database, or a group of databases that are in a single storage group.
For example, you can configure a Recovery Storage Group to recover mailbox items that were deleted from a user's mailbox. Follow the steps given below to create a Recovery Storage Group. Open Exchange System Manager and expand Exchange organization > Servers.
Right- click the server name, and then click New > Recovery Storage Group. Browse and enter the Transaction Log Location.
Ensure that the location of the Recovery Storage Group has enough memory space for Transaction Logs. Browse the System Path Location. Click OK. Right- click on the newly created Recovery Storage Group and select Add Database to Recover. Select the Exchange database that you want to recover, then click OK. Click the Database tab and ensure the location of the database files are on a drive that has sufficient space.
Select the This database can be overwritten by a Restore check box. Click OK. If the database to be restored is still in production, go to the properties page for the production database and ensure that this option is disabled in order to safeguard the database from being overwritten. Applies to: Exchange 2. Before you use the Exchange Database Agent in Database Availability Group (DAG) environments, you must configure a master client and select the appropriate server. The master client stores the configuration information for all member servers, and coordinates backup and restore operations for different servers. Sometimes the master client is also referred to as a pseudo client.
From the Comm. Cell Browser, right- click Client Computers, and then click New Client > Application > Exchange DAG. The Exchange DAG Client Creation dialog box appears. From the AD Domain Name list, select the appropriate Active Directory domain name. If no domain name was configured previously, you must enter the domain name and the appropriate credentials. Click Discover. If the AD Server Credentials dialog box appears, enter the Active Directory credentials.
Click OK. DAG Member Servers are listed with their fully- qualified domain name. They appear highlighted if the Exchange Database Agent of the current software release is installed.
From the DAG Servers list, select the appropriate server. From the Member Servers list, select the appropriate servers. In the Client Name box, type a name. Click OK. The master client is created.
In a DAG configuration, you can configure to run backups from any of the available servers. Manual server selection facilitates backups of both mailbox and public folder databases. From the Comm. Cell Browser, navigate to the Master Client's subclient, right- click and select Properties. Click the Server Selection tab. Select Manual selection and click Discover. A list of all discovered databases will be listed under Server Associations. Select the server from which you want to backup the databases.
Click Ok. In a DAG configuration, the default is to run backups from the next available passive server to enhance performance.